Malware (a combination of the words malicious and software) is software code designed to infiltrate and/or damage a computer system without the owner's knowledge.  Sometimes people use the term "computer virus" interchangeably with the term malware. Surveys report that 95 per cent of people use antivirus software, but infections remain common.
Sometimes people use the term "computer virus" interchangeably with the term malware. Surveys report that 95 per cent of people use antivirus software, but infections remain common.
Computer professionals consider viruses to be a subset of malware. Malware includes computer viruses, worms, adware, spyware, trojan horses, and other malicious software.
There is a war underway between malware professionals from companies like Norton and McAfee, and the bad guys who are often from Eastern Europe. As of today, the bad guys are winning.
Barack Obama has promised to appoint a "Cyber Czar" to lead the fight. Obama emphasized that the cyber threat is "one of the most serious economic and national security challenges we face as a nation. It's also clear that we're not as prepared as we should be, as a government or as a country."
An unacceptable percentage of PCs are infected. According to Harvard Law professor Jonathan Zittrain's interview on 60 Minutes, 30% of computers have malware on them at any one time. PandaLabs Security estimates that just one virus, Conficker, infects 6% of the world's computer population.
According to Symantec, unsolicited e-mail (spam) makes up over 90 percent of all messages on corporate networks. Symantec further reported that almost 60 percent of spam is now generated by malware botnets, computers that have been hijacked by criminals. Dunbot, the worst of the spamming botnets, generates over 18 percent of all spam.
Malware gangsters now commonly use websites that sell fake anti-virus software or offer bogus downloads to distribute their malware. Video "Codecs", which is software for viewing on-line video, is a commonly infected download.
Panda Security estimates that up to 35 million computers worldwide may be infected with fake antivirus programs each month.
Industry Response
Intel technical marketing manager Steve Cutler predicts that malware will eventually be conquered with hardware-based techniques that protect the computer at the deepest level.
Intel is promoting its 'trusted execution technology' which is a set of processor hardware extensions and chipsets that have security characteristics such as measured launch and protected execution. This design is capable of creating an environment in which applications can run within their own memory space, protected from all other software on the system. The success of this hardware-based security is dependent on software vendors designing their products to utilize this security. Intel predicts that once it is known that there is a solution that can successfully address the problem of malware, the market will demand that software vendors comply.
Conficker
The Conficker Worm is the latest major challenge to the system. This worm has already infected several million computers. On April 1, the worm on infected computers connected over the Internet to the “botnet”, a network of host computers set up by the worm’s creators. Security professionals know which Internet server computers are the hosts for the botnet, so the system was prepared, but the worm infection rate is now too high for containment. Microsoft has offered a $250,000 bounty for the identity of the Conficker hoodlums.
Security professionals have methods for measuring the rate of computers infected. Using these techniques, PandaLabs Security has reached the conclusion that about 6% of computers worldwide are infected with Conficker, and about 50,000 new PCs are infected every day, according to Guy Bunker, a computer security expert at Symantec. According to stats from the Conficker Working Group, the number of unique IPs detected as infected with Conficker has risen in June, from 3.7 million on May 31, to 5.1 million at the end of the month.Worldwide Conficker Infection Map
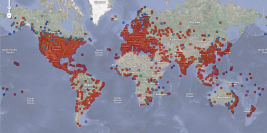
Conficker takes advantage of a design flaw in Windows. If a computer is current with its security updates, the design flaw has been closed since last October. But many people do not stay current, either because they are running a pirated copy of Windows, or from lax computer housekeeping. Unlike most malware, Conficker is very good at spreading because it can identify vulnerable PCs on its own and doesn't require human interaction to infect a computer.
The worm’s creators are in position to generate enormous levels of spam, spread new malware, or do damage to web resources. In recent months, Conficker's creators have updated the worm so that infected computers have been given new ways to communicate.
"The worm did exactly what everyone thought it was going to do, which is update itself," security expert Dan Kaminsky, who helped develop a widely-used Conficker scanner in the days leading up to April 1, told us: "the Conficker developers have cemented their ability to push updates through any fences the good guys have managed to build in February and March."
As far as what comes next? More waiting. Good methods now exist for detecting (Conficker Test) and cleansing Conficker from infected machines on a network (and, let's not forget, a months-old security patch from Microsoft is all you need to protect yourself), but by now the size of Conficker's infected army of nodes spread around the world is big enough to function with devastating consequences even if most PCs are secure.
Gumblar
Gumblar, a malware worm, is attacking computers through vulnerabilities in older versions of Adobe's PDF reader and Flash player software. The worm can redirect the user's Google search results to sites that download more malware onto the machine or allow criminals to conduct "phishing" attacks. Gumblar will disable the links found on the Google search results, and instead connect the web browser to sites that further compromise the system. Although Gumblar is not new, it has resurfaced in the new form recently.
"The Gumblar attacks have morphed again," said Mary Landesman, a senior security researcher with ScanSafe.
The rate of Gumblar infections increased by more than 200% last week. Sophos estimates that Gumblar is currently responsible for 42% of "drive-by" malware on websites.
Detecting an infection is complex, and not fool-proof. According to ScanSafe to find out if your PC has been hijacked by Gumblar, locate the file sqlsodbc.chm in the Windows system folder: C:\Windows\System32.
Obtain the Sha1 of the installed sqlsodbc.chm using FileAlyzer , a free tool for obtaining the Sha1 of a file. Sha1 is an automatically generated digital identifier for files designed by the National Security Agency (NSA), and used by security applications to confirm that a file is correct.
Compare the obtained Sha1 code and the file's size to the list located on the ScanSafe STAT Blog.
If the Sha1 and corresponding file size do not match with a pair on the reference list, it's a potential sign of a Gumblar infection.
Adobe
Adobe modules are now frequently targeted by the malware bad-guys. This includes both Adobe Flash player and Adobe Reader. Adobe Reader is the program frequently used to distribute documents such as technical manuals.
"Adobe Reader is the new Internet Explorer," said Mikko Hypponen, chief research officer with the Finnish antivirus company F-Secure.
According to Hypponen, of the total malware attacks recorded this year, 50 per cent have exploited the six known security vulnerabilities in Adobe's PDF products. Last year (2008), it was Microsoft Word which was most often the target, with about 35 per cent of total attacks. Attacks on Adobe Reader this year are up by approximately 1800%, as compared to the same period last year.
Hypponen suggested referring to pdfreaders.org for a list of free alternatives to Adobe Reader that may be more resistant to the malware. He warned that at the time of Internet Explorer 6's security problems, many people switched over to using Firefox, but as that browser gained significant market share, it also drew the malware hacker attention.
Hypponen said that Adobe's lack of regular security updates is a significant part of the problem. In late July, Adobe released patches for both the Flash player and Adobe Reader.
Adobe has a patch the "Zero-Day" security issue that has been using to break into computers through the Adobe Flash module.
Adobe's patches close security holes in the integer overflow, stack overflow, and heap overflow code modules that could allow to remote control of the software.
Users of Adobe Flash Player 9.x and 10.x or earlier versions should update to Adobe Flash Player 9.0.246.0 and 10.0.32.18. In addition, Adobe also recommends users of Adobe AIR version 1.5.1 and earlier versions update to Adobe AIR 1.5.2.
Users of Adobe Reader 9 and Acrobat 9 or earlier versions should update to Adobe Reader 9.1.3 and Acrobat 9.1.3.
Microsoft Office
The office suite has frequently been the target of attack. This is not surprising, given the popularity of the line. Outlook, Word, Excel, and Powerpoint have each been the target of malware attacks.
Microsoft recently issued a statement that it will no longer provide security updates for Office 2000 products. This is Microsoft's standard policy of a 10 year support period. It also provides incentive for users to upgrade to newer versions of Microsoft's products.
AntiVirus professionals are sometimes very vocal in their contempt of Microsoft Office. Kaspersky Lab has pointed out that Microsoft should secure its Office suite, and not rely on the "Band-Aid over a gaping wound" method of issuing patches for each vulnerability, but instead should address the technology that powers and processes OLE objects.
OLE is Microsoft's interprocess communication mechanism based on the Component Object Model (COM). Microsoft sometimes just calls the technology "automation".
A common method of attack involves a file posted on the Internet for download. When the file is opened, the malware is activated.
Fake Harry Potter Downloads
There is a scam out there in the form of Harry Potter downloads. This is an old trick, in a new lure. Video Codecs have been used before to spread malware. This time the lure is 'Watch "Harry Potter and the Half-Blood Prince". The scam involves getting you to download a "Streamviewer" that the site leads you to believe is needed to see the movie, but is actually malware. This is a "Trojan Horse".
There are ways to detect the scam. One of the ways is to carefully check the link. At first glance, it may look OK, but under close scrutiny, the URL will be suspicious. You can check downloads by uploading the file to VirusTotal.com, where the file will be tested.
Microsoft Windows 7
Windows operating systems are used in about 90 percent of the world's computers. Windows 7 is in beta site testing, and should be generally available for the upcoming Christmas shopping season. But Microsoft has warned that cybercriminals are already selling booby-trapped versions of the software.
"It's so important for customers to get their copies of Windows from a trusted source," Joe Williams, general manager, Worldwide Genuine Windows at Microsoft.
"With Windows Vista, we made significant strides in reducing the threat pirated copies posed to customers, our partners and Microsoft software, and we anticipate we'll do even better with Windows 7," Williams said.
Microsoft research estimates that as many as a third of the company's customers worldwide are running counterfeit copies of Windows.
"We see many cases of customers who wanted to buy genuine software and believed they did, only to find out later that they were victims of software piracy," Williams said.
In the case of Windows 7, the pirated software may include compromised security and tailored malware.
Reference
Virus: A virus is computer program code that will try to spread from one file to another on a single computer and/or from one computer to another. A classic virus is not an independent program, but instead, is code that attaches to an existing file on a computer. Kapersky Virus Lab reports that 200-300 new virus samples are received in their office every day.
Trojan Horse: Trojan Horses are a subset of viruses. They
get their name by the fact that they pretend to be legitimate.
Worms: A worm is a self-replicating computer program. It sends copies of itself to other computers over the Internet or other network. Unlike a virus, a worm is an independent program.
Adware: Adware generates advertisements such as pop-up windows on Web pages. The objective of adware is to earn income from advertisers.
Spyware: Spyware is a program that tracks your habits. Because it is a computer program, spyware can ensure that the spyware keeps running and may influence web navigation.
Most of time we think about Malware as the product of some pimply-faced geek. But recently, spyware didn't come from some Eastern European hacker ring. It came from one of the premier names in U.S. commerce: Sears.
"It's quite off-putting to think of a company tracking these kinds of things about you," said Benjamin Edelman, a longtime spyware researcher and an assistant professor at the Harvard Business School.
Rick Quaresima, Federal Trade Commision lawyer said the agency's primary concern was that consumers were likely unaware of how much information Sears was collecting. Sears monitored "nearly all of the Internet behavior that occurs on consumers' computers," and also collected data about the users' computers, printers, and other devices, said the FTC.
For most Malware today, the primary intent is not damage to the computer. If the user does not recognize the infection, then the program can steal passwords, credit card numbers, or use the computer to send spam to other computers on the network.
According to FBI Deputy Assistant Director Steve Martinez, Eastern European gangs are turning increasingly to cybercrime. He said the FBI had urged law enforcement agencies in other countries to go after the gangs.
Most malware is not the result of a rogue geek, but instead is the product of adult professional criminals.
"There's a lot of money in the Internet. On the last count of malware I did, only 10 percent was written by teenagers. Ninety percent is developed by criminals. This malware is designed for criminal needs such as stealing money, distributing spam and Internet rackets." said Eugene Kaspersky, head of antivirus research for Kaspersky Labs.
Kaperky further said that criminals are turning to the Internet because of the lack of security and policing.



0 Discussion:
Post a Comment